SAML 2.0 Configuration
Device42 integrates with SAML 2.0 in conjunction with AD or LDAP user synchronizations to provide Single Sign On (SSO) support in Device42. Once users are added to Device42 via Active Directory or LDAP, they will automatically be logged into Device42 when they load the site.
Since authorization is handled by Device42, the SSO functionality only works if the user account already exists within Device42 before the user logs in.
SAML configuration varies between providers, but we'll provide the steps for configuration with Microsoft ADFS, Okta, and Onelogin below as examples. Device42 SSO should also work with any SAML 2.0 compatible Identity Provider and has been confirmed to work with IDaaS providers, Centrify, and PingIdentity's PingOne and PingFederate.
Should you need further assistance, please contact Support.
Microsoft ADFS Configuration
Add a new relying party trust.
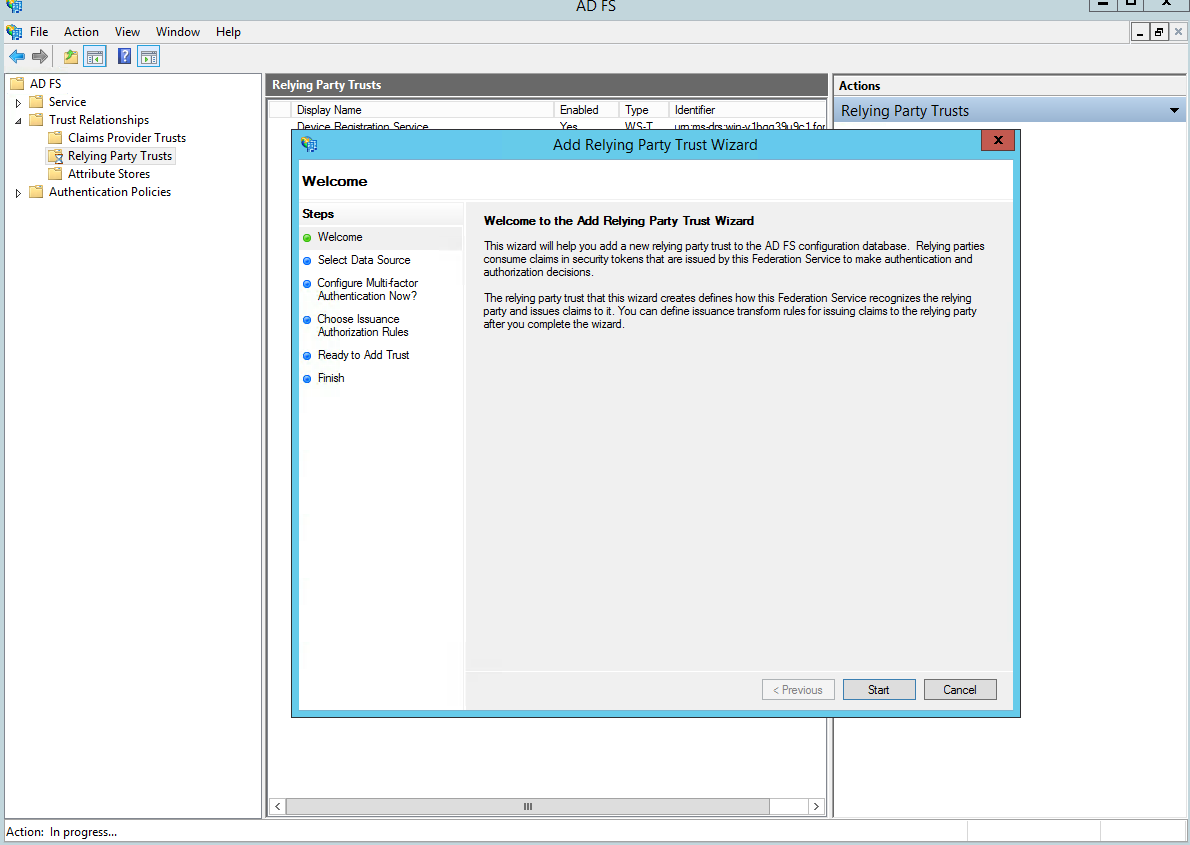
Next screen: Add data manually.
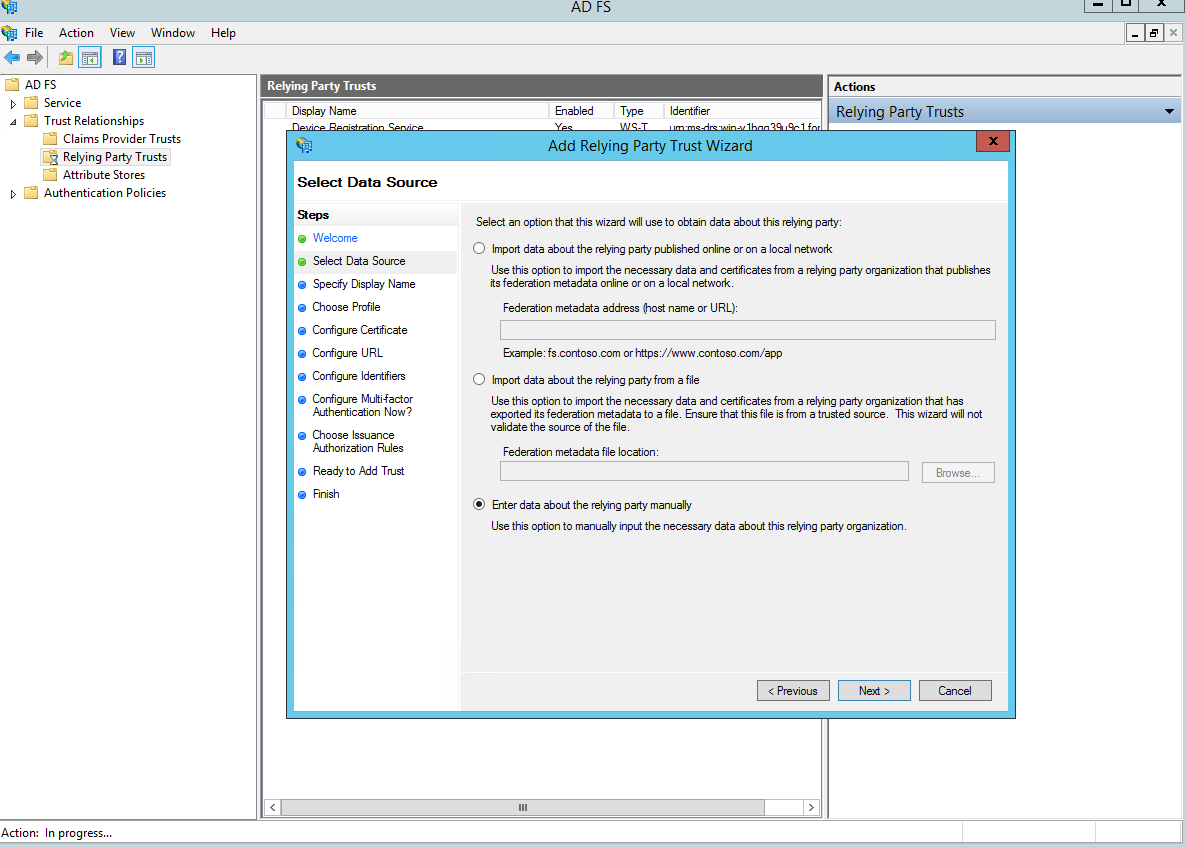
Next screen: Specify your app display name.
Next screen: Choose AD FS profile.
Next screen: Choose SAML 2.0 SSO and set proper D42 ACS URL: https://___device42___url/saml2_auth/acs/.
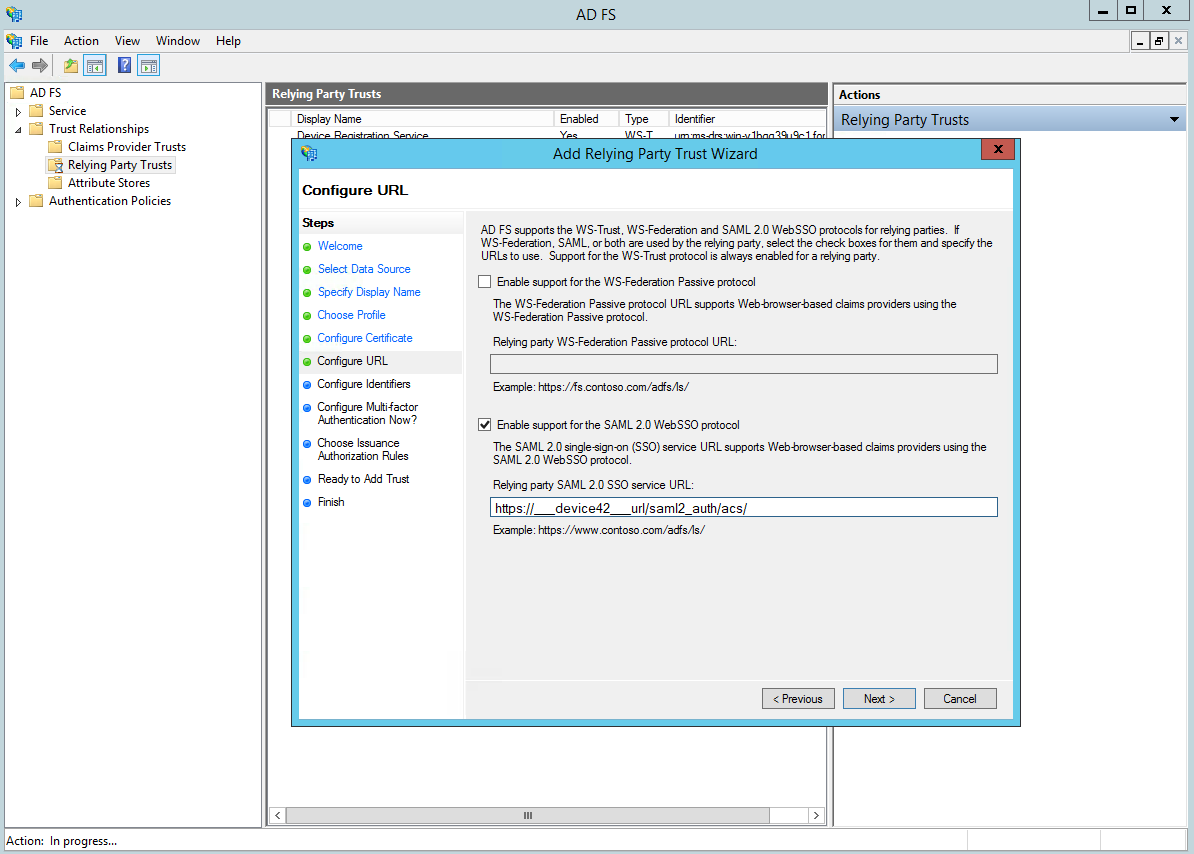
Next screen: Set identifiers access: https://___device42___url/saml2_auth/acs/.

Next screen: Permit all users.
Next screen: In the claims section (click Edit claims on the relying party / automatically go to this section after initial setup), add the following claims:
-
The
usernameclaim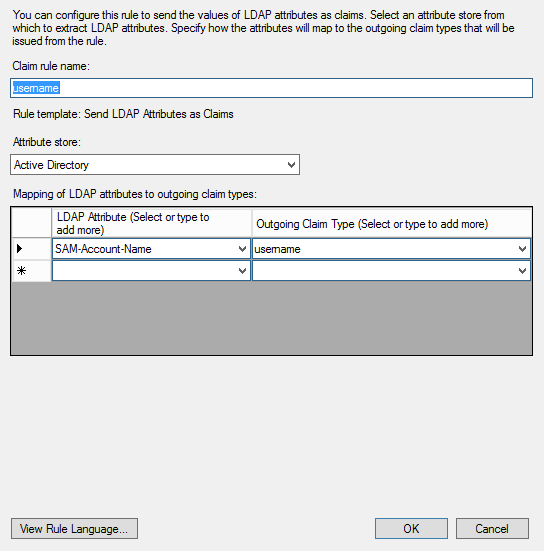
-
The
nameidclaim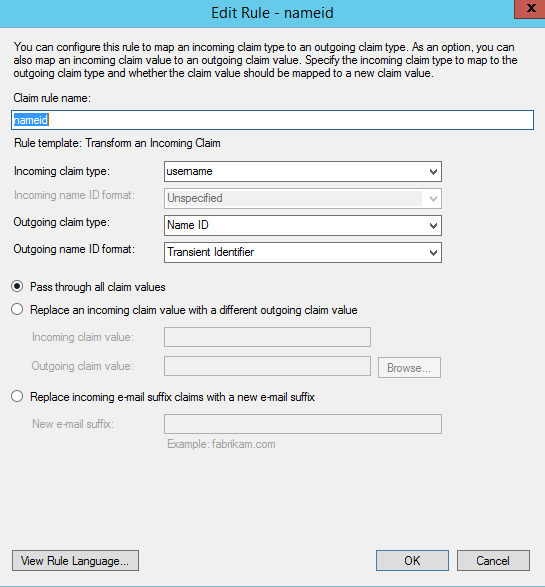
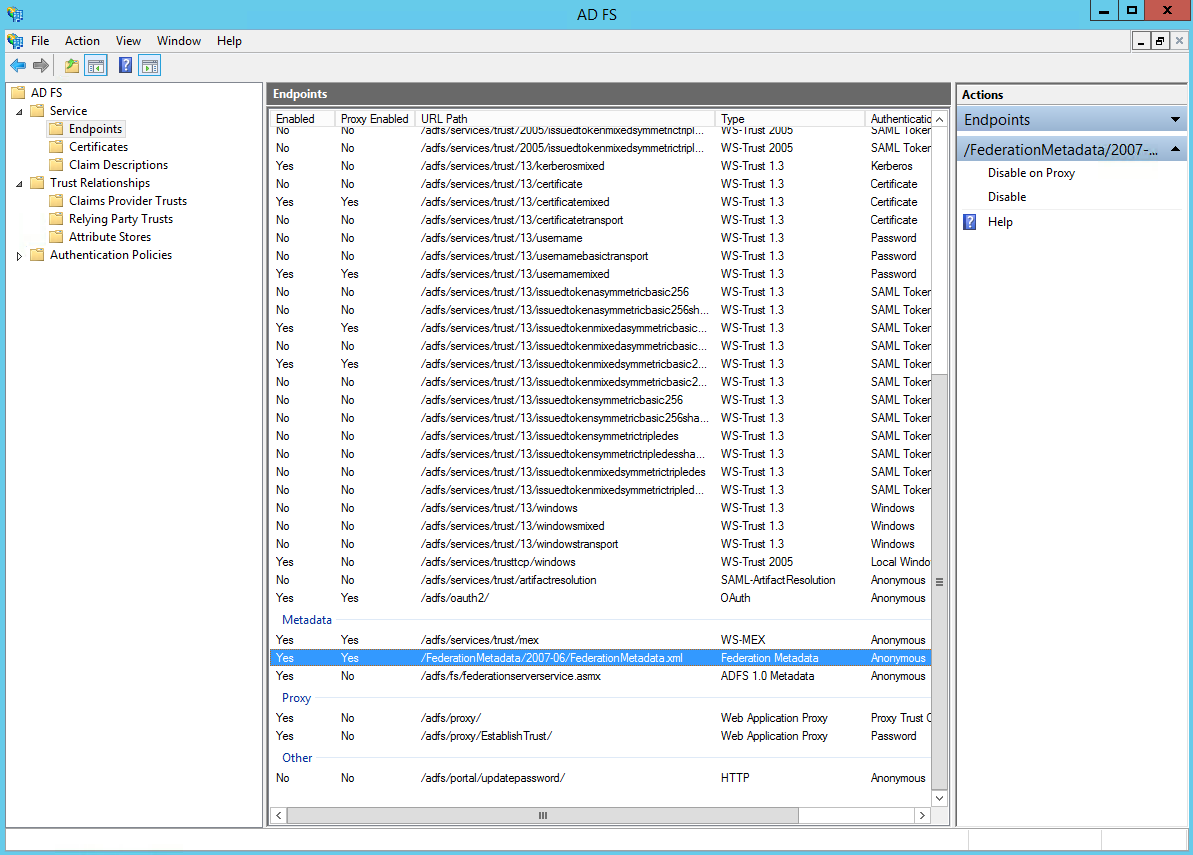
Then, copy the metadata URL from the endpoints.
If you receive a time synchronization error, please write this command in PowerShell:
Set-ADFSRelyingPartyTrust -TargetIdentifier "" -NotBeforeSkew 5
Azure AD Configuration
-
Navigate to Azure AD in the Azure portal via Enterprise Applications > New Application > Create your own application. Give your app a name (the app shown in the screenshots is
Device42SAML) and select the third option Integrate any other application..., then click Create.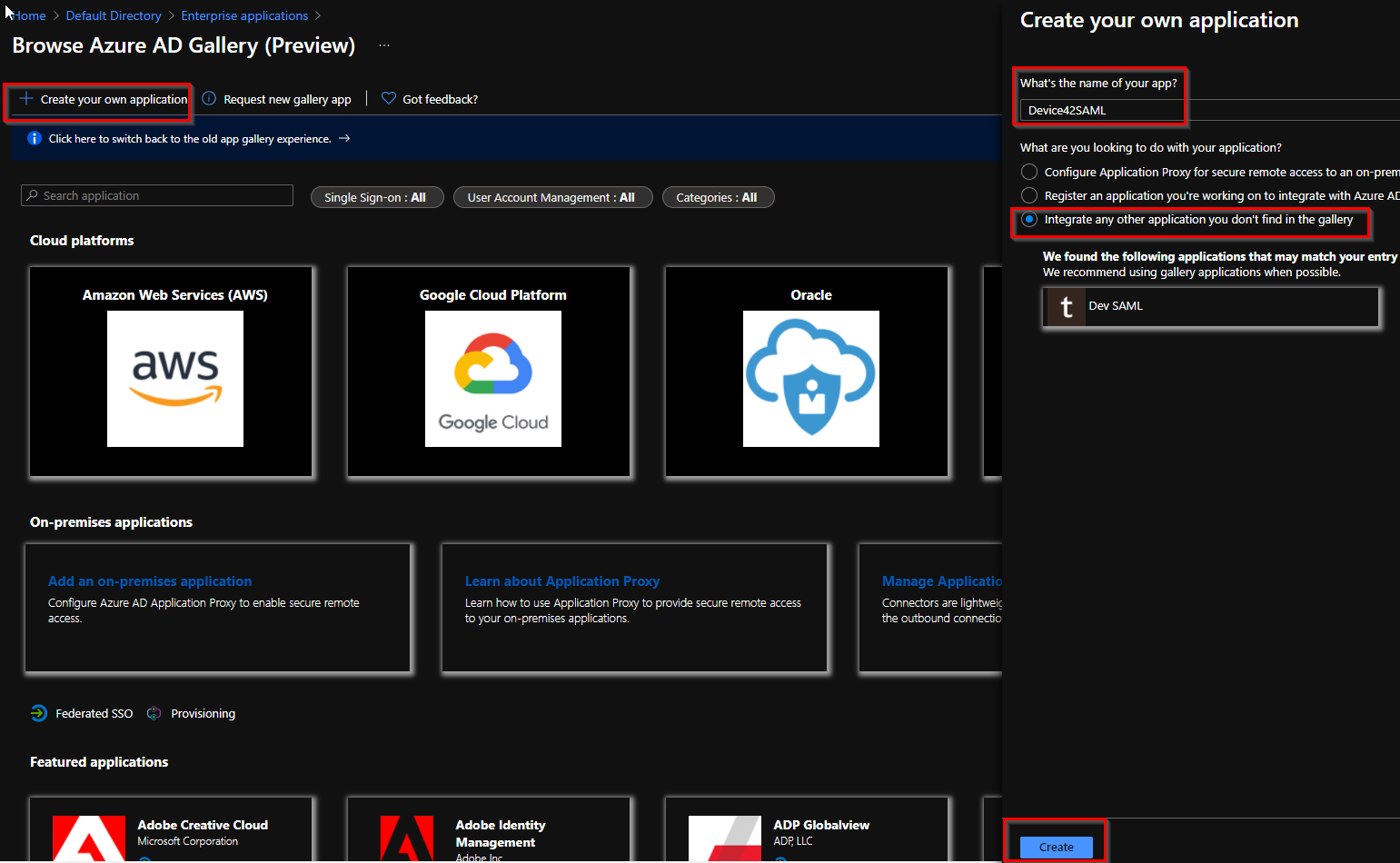
-
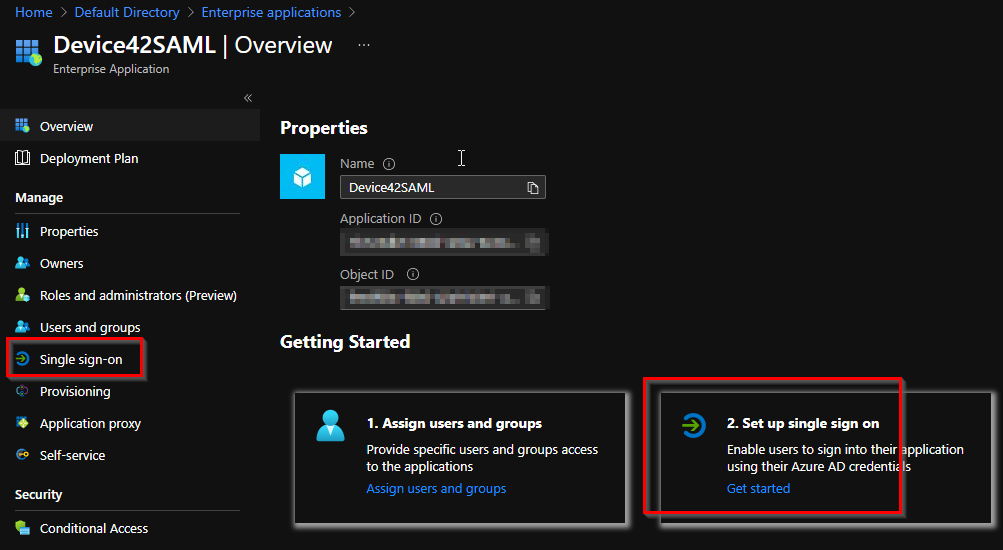
Open your newly created enterprise app. Then, under the Getting Started section, select the second option, Set up Single sign on. Alternatively, select Single sign-on under Manage in the left-hand toolbar.
-
In the first section, Basic SAML Configuration, enter
https://<D42-FQDN-or-IP>/saml2_auth/acs/in the Identifier (Entity ID) and Reply URL (Assertion Consumer Service URL) fields.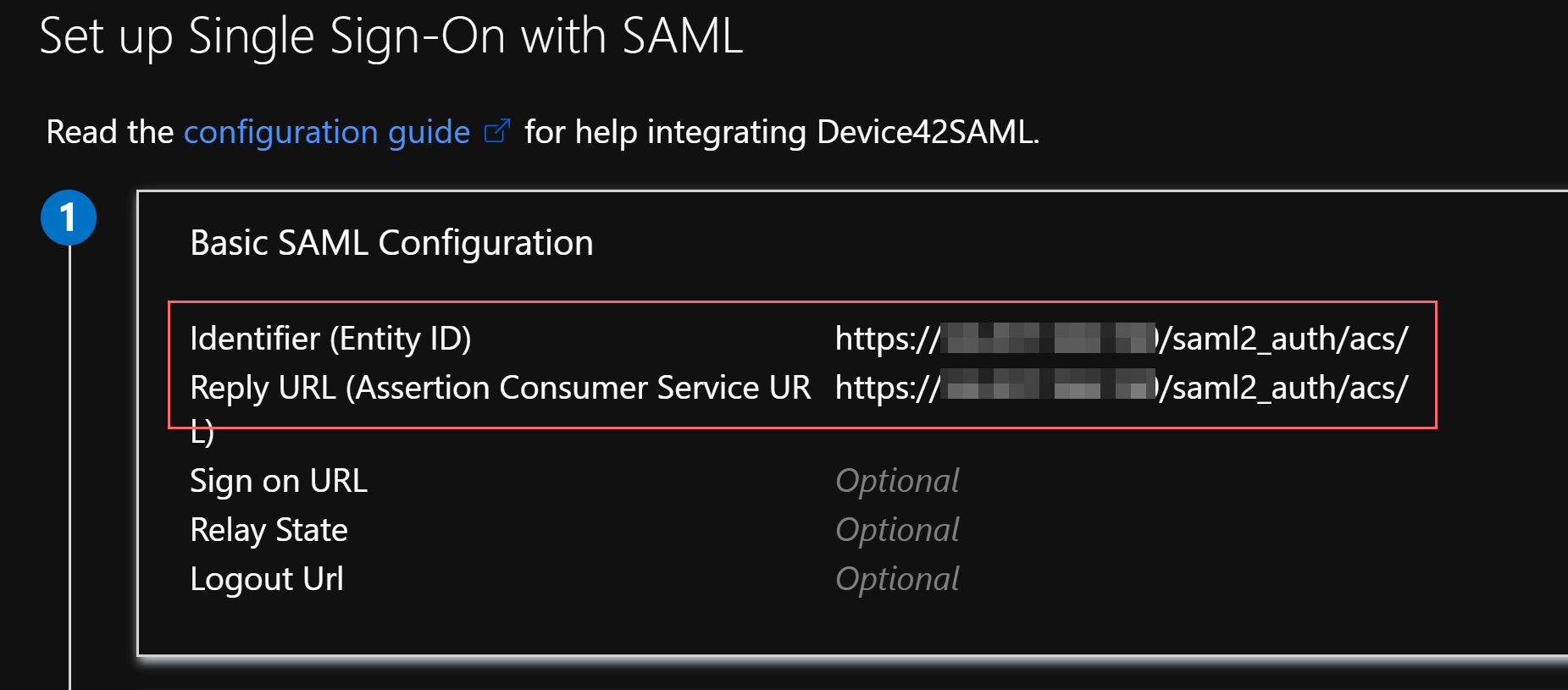
-
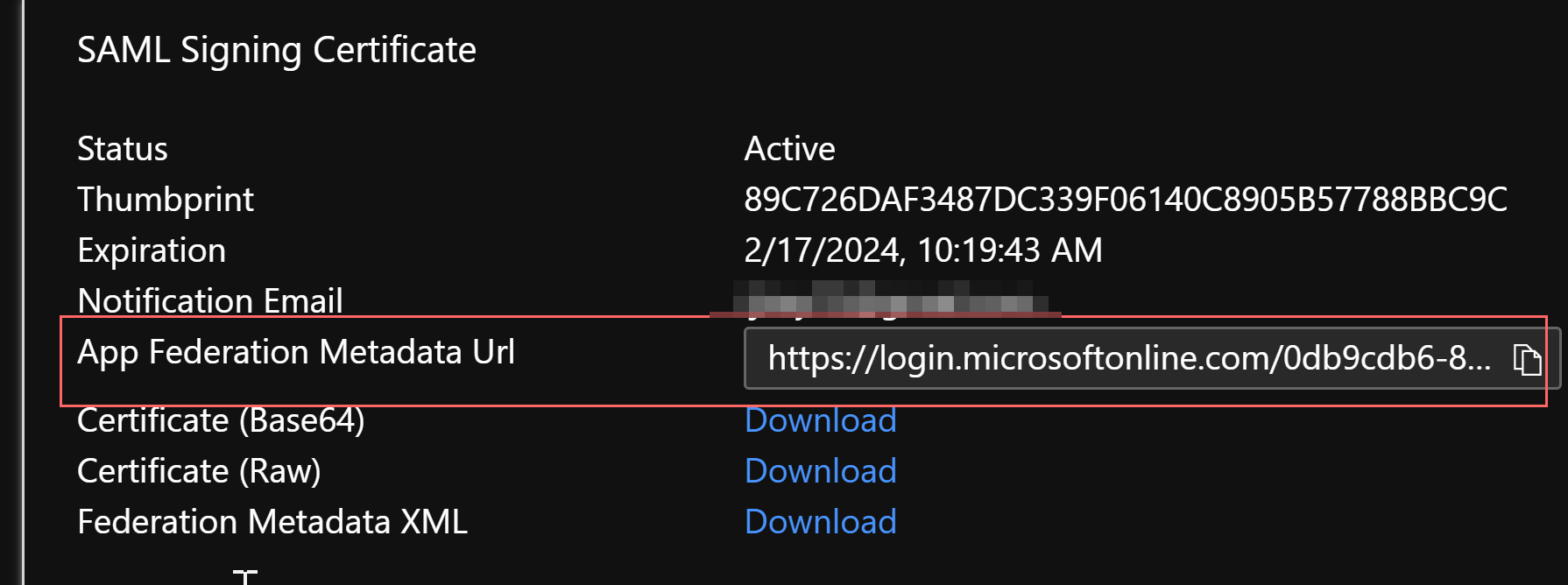
Navigate to the Device42 Appliance Manager and go to Global Settings > SAML/SSO Settings. Copy the App Federation Metadata URL in the SAML Signing Certificate section for the enterprise app you created in Azure AD, and paste the URL into the Metadata auto conf url field in the Device42 Appliance Manager.
-
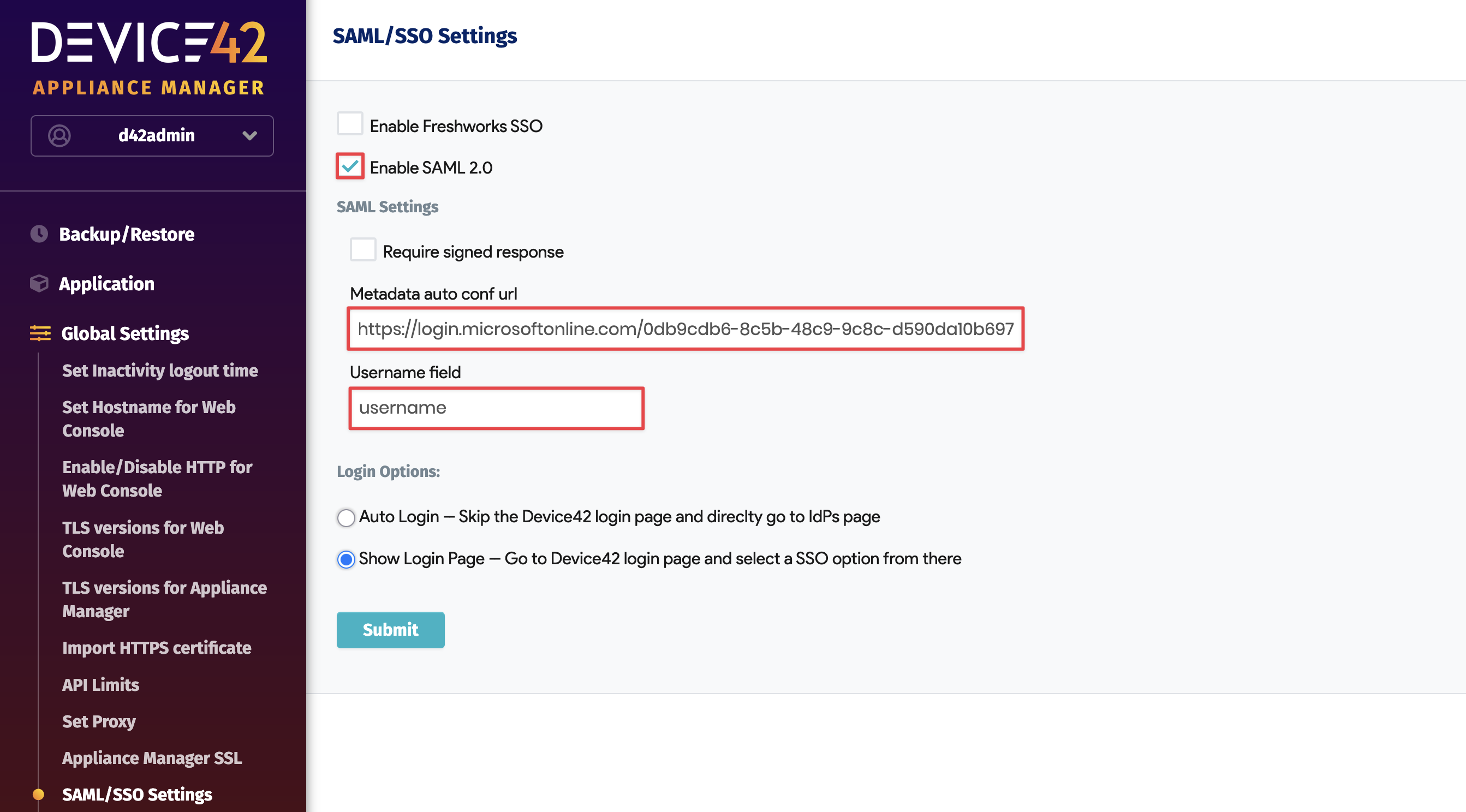
While still in the SAML 2.0 Settings of the Appliance Manager, enter
usernameor another appropriate SAML attribute in the Username field. Unless you have signed responses configured on your Azure AD provider side, keep the Require signed response box unchecked; otherwise, you'll get an unavailable page message.Azure's built-in claims like
emailaddressmay not work with Device42, even though they appear in the Azure interface, because the built-in claim uses a namespace URI format. The solution is to create a new claim foremailaddressin your Azure AD enterprise app, map the claim to the user attribute, and use the custom claim name in the Device42 SAML Username field.Save and restart the appliance from the VM console menu. You may wish to complete steps 6 and 7 before saving or restarting, so that you can still log in to Device42 and create users with the local admin account you've used so far.
-
Assign users or groups to the SAML enterprise app you created in Azure AD. These should be users or groups that you want to allow authentication into Device42 via this SAML integration.
-
For any users associated with the enterprise app in Azure AD, create the user in Device42 using the appropriate Azure AD value with a dummy password. The integration does not pull and create users directly from Azure AD, so the users must be created within Device42 prior to any attempt to authenticate via Azure AD.
-
Once the above has been completed, you should be able to log in to your Device42 instance with your Azure AD credentials.
Okta Configuration
In Okta, click the Admin button:
Click the Applications button.
On the Applications page, find and click the Add Application button.
Choose Create New App.
Select Web as the Platform and select SAML 2.0 as the Sign on method.
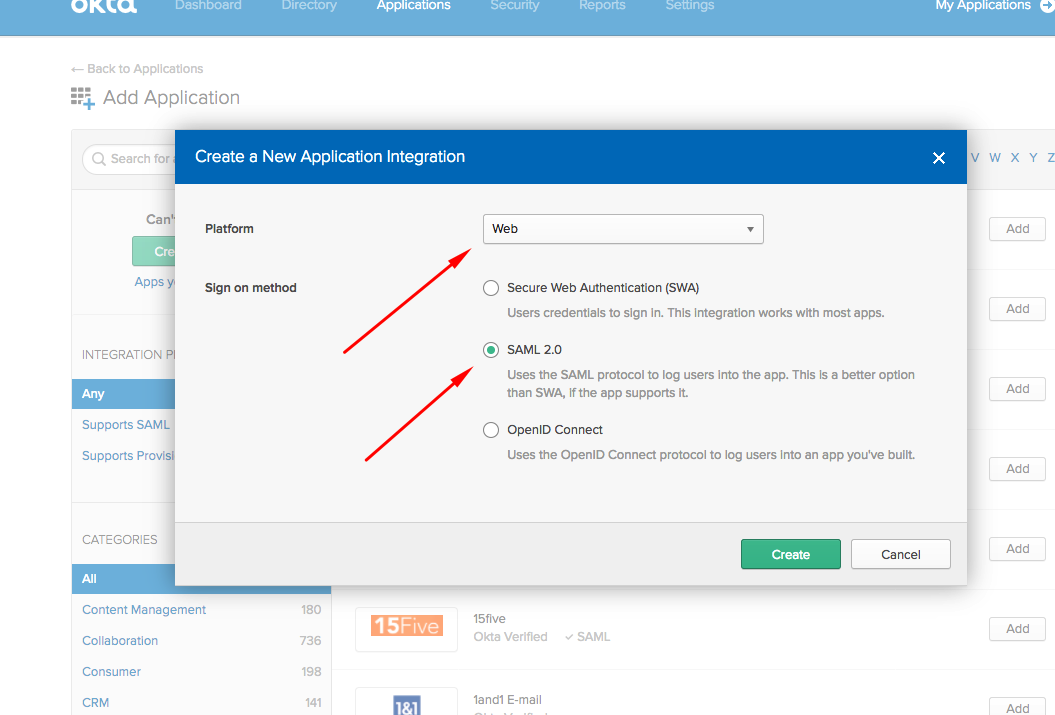
Set your application preferences and click Next.
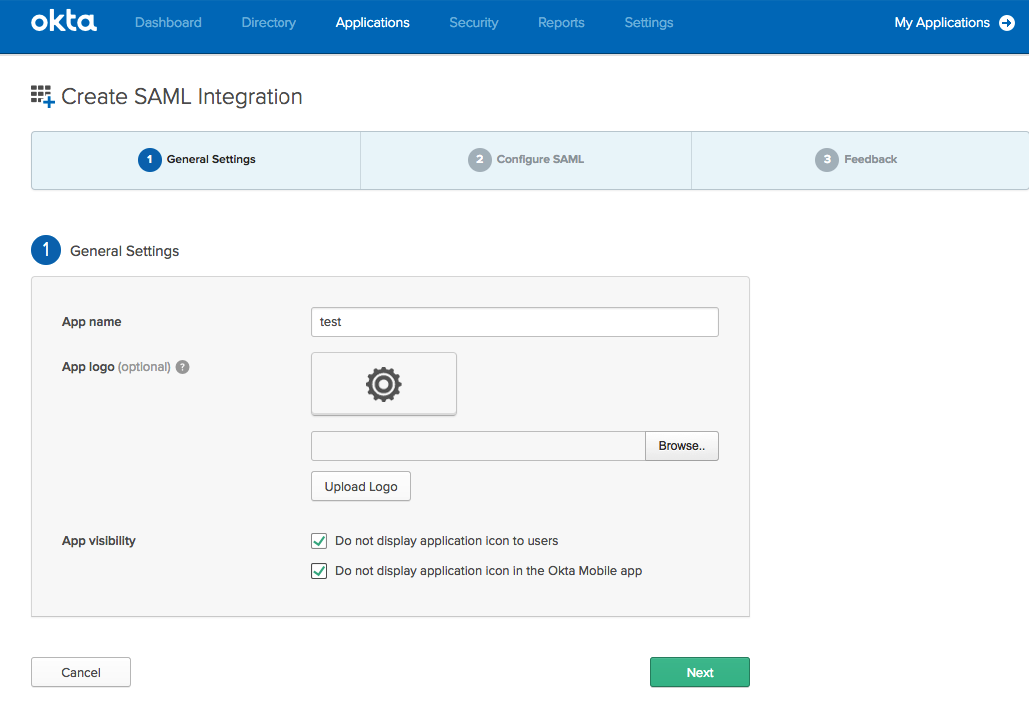
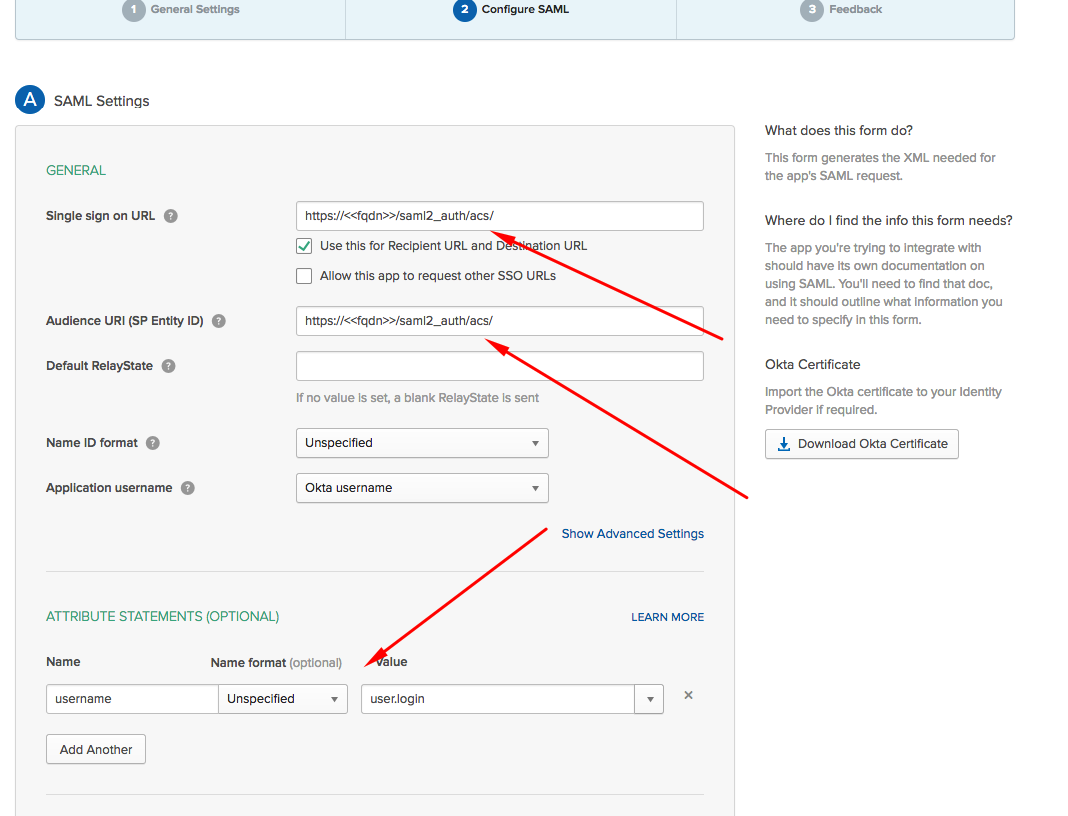
On the next page, set up the ACS URL and field mapping. Enter https://yourdevice42address/saml2_auth/acs/ for both the Single sign on URL and the Audience URI (SP Entity ID) fields. In the Attribute Statements section, the Value should be the same AD or LDAP attribute that your users will use to log in to Device42. Note the attribute statement Name, as it is needed in the Device42 Appliance Manager configurations.
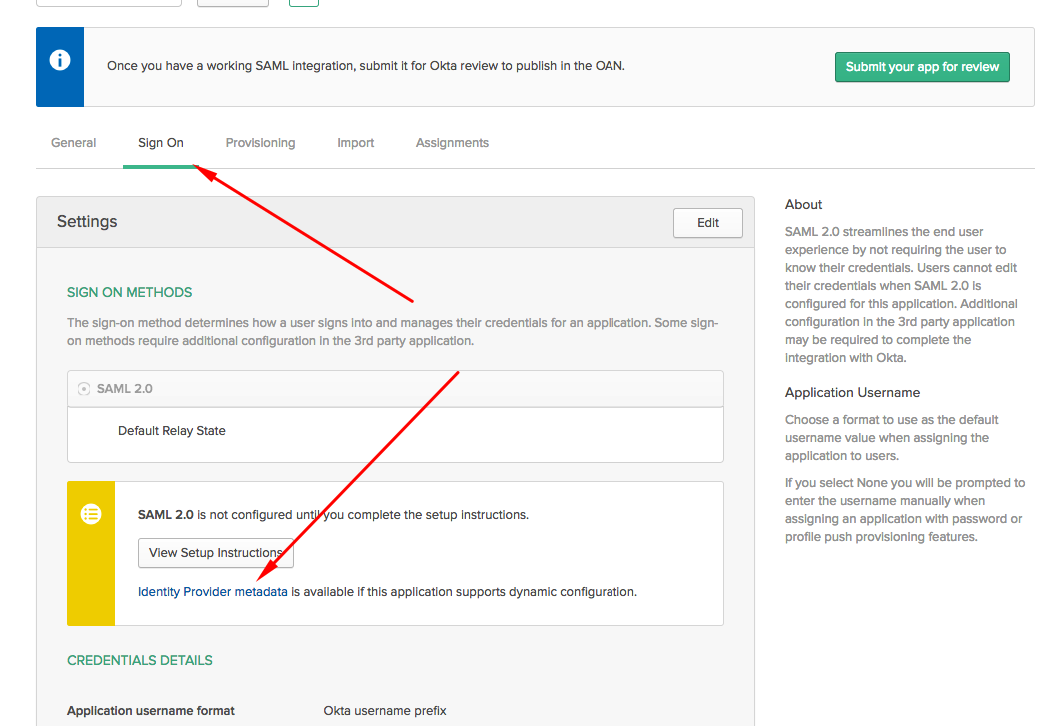
Click Next and finish the setup. Open your application settings, go to the Sign On tab, and copy the URL of the Identity Provider metadata link. You will use this URL as the Metadata auto conf url in Device42's Appliance Manager.
OneLogin Configuration
To configure SAML 2.0 integration between OneLogin and Device42, you have to create a SAML2 connector app in OneLogin. Then, you need to add users to the SAML2 connector app so they can log in via a OneLogin account.
Creating the SAML2 Connector App
-
Create and log in to your OneLogin account.
-
Create an app connector in OneLogin:
- Go to Applications > Applications.
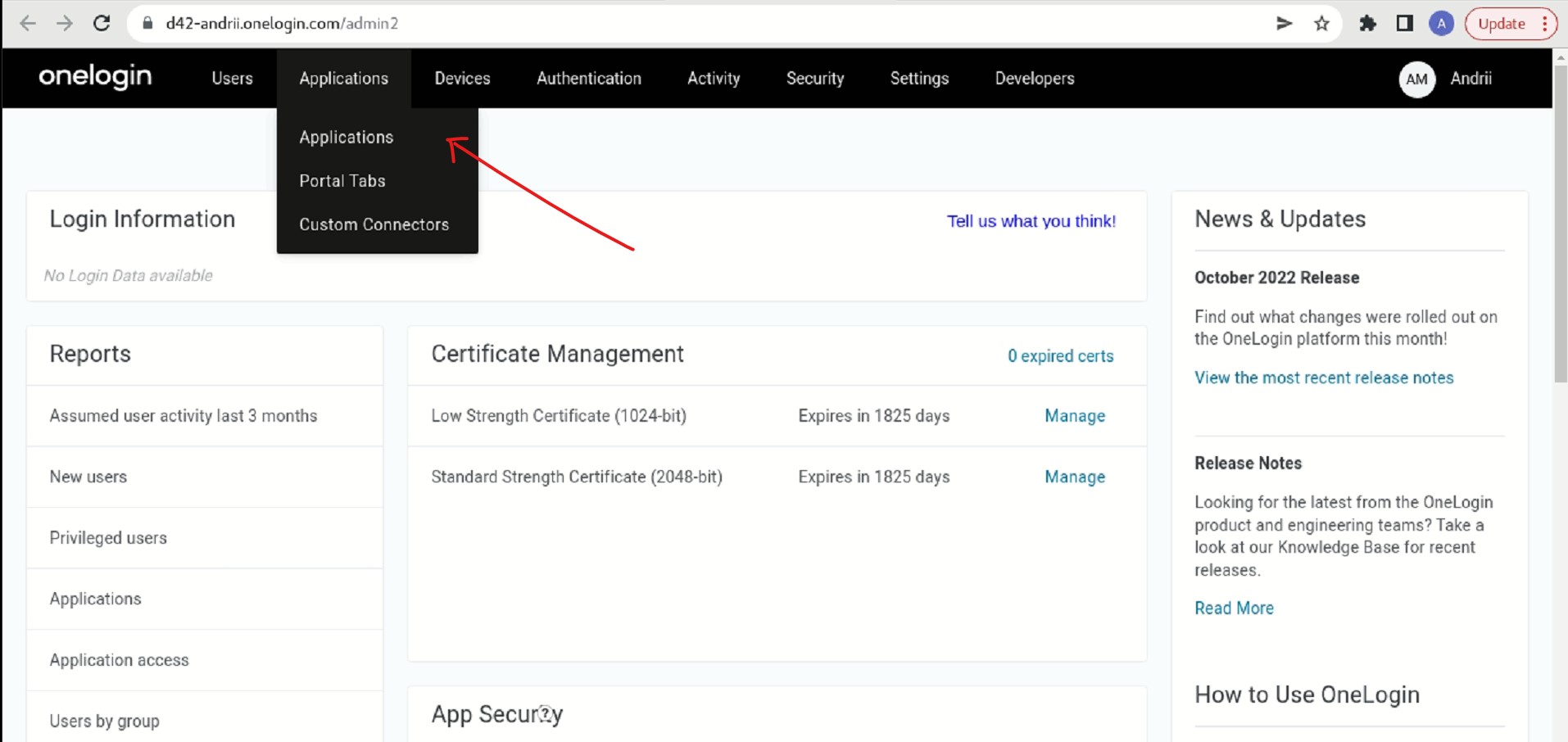
- Click Add App.
-
Search for SAML custom connector and select SAML Custom Connector (Advanced).
-
Type a display name and Save.
-
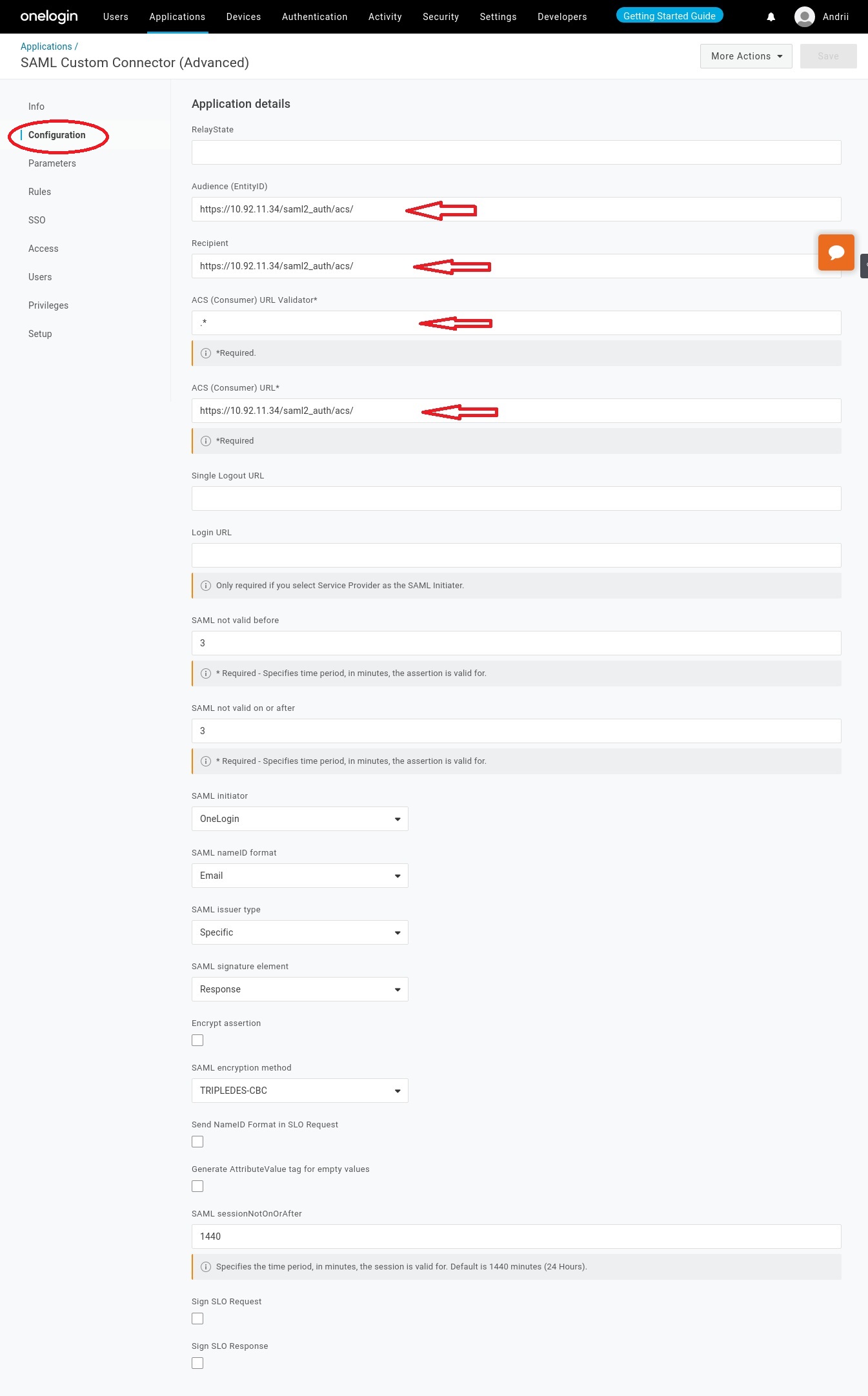
Go to the Configuration tab:
- Put the value,
https://<<fqdn>>/saml2_auth/acs/, in the Audience (EntityID), Recipient and ACS (Consumer) URL fields. - Put
.*in the ACS(Consumer) URL Validator field. - Save.
- Put the value,
-
Go to the Parameters tab and add a new field by clicking on the plus icon.
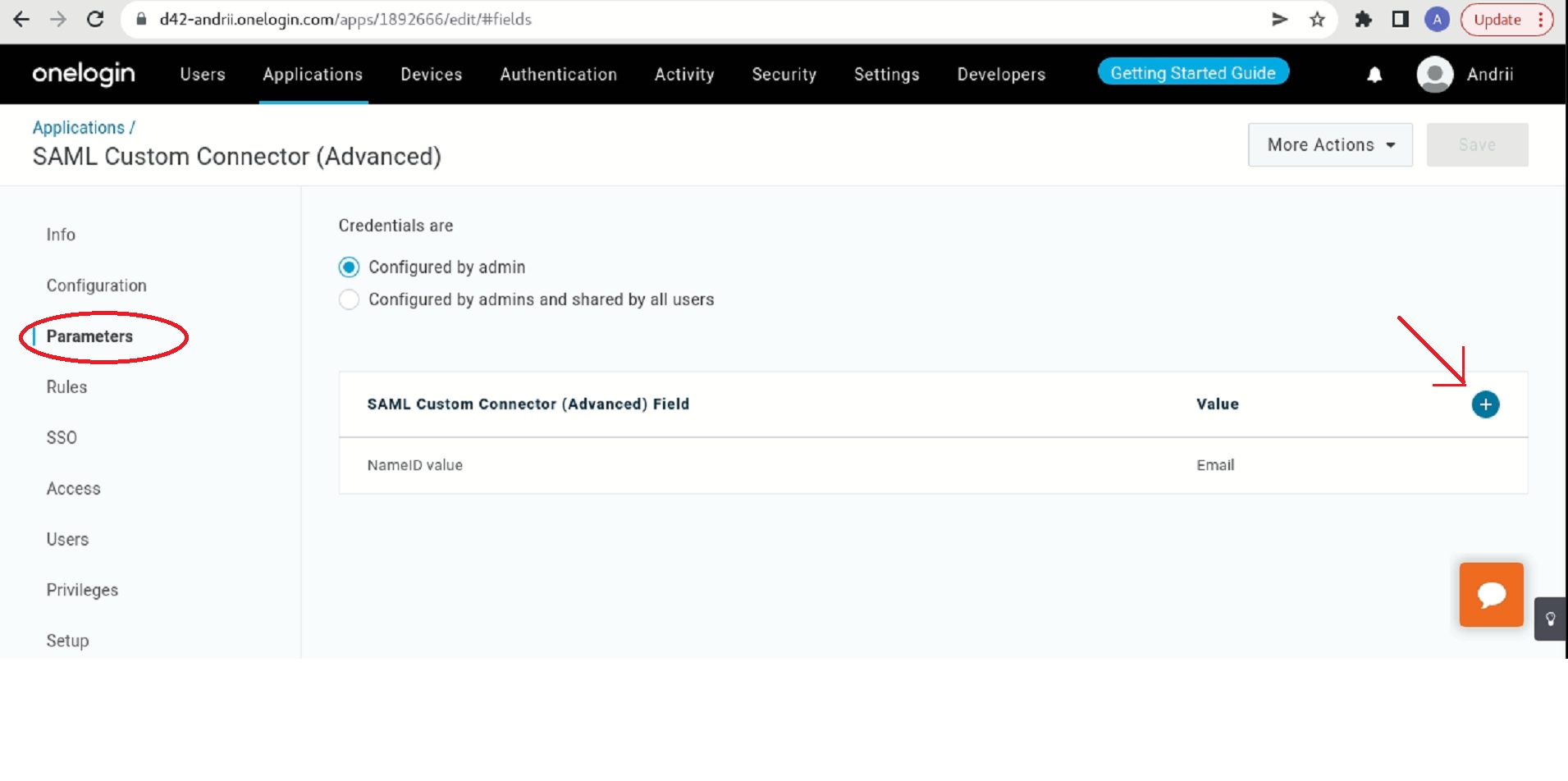
- Type
usernameas the Field name. - Select the Include in SAML assertion checkbox.
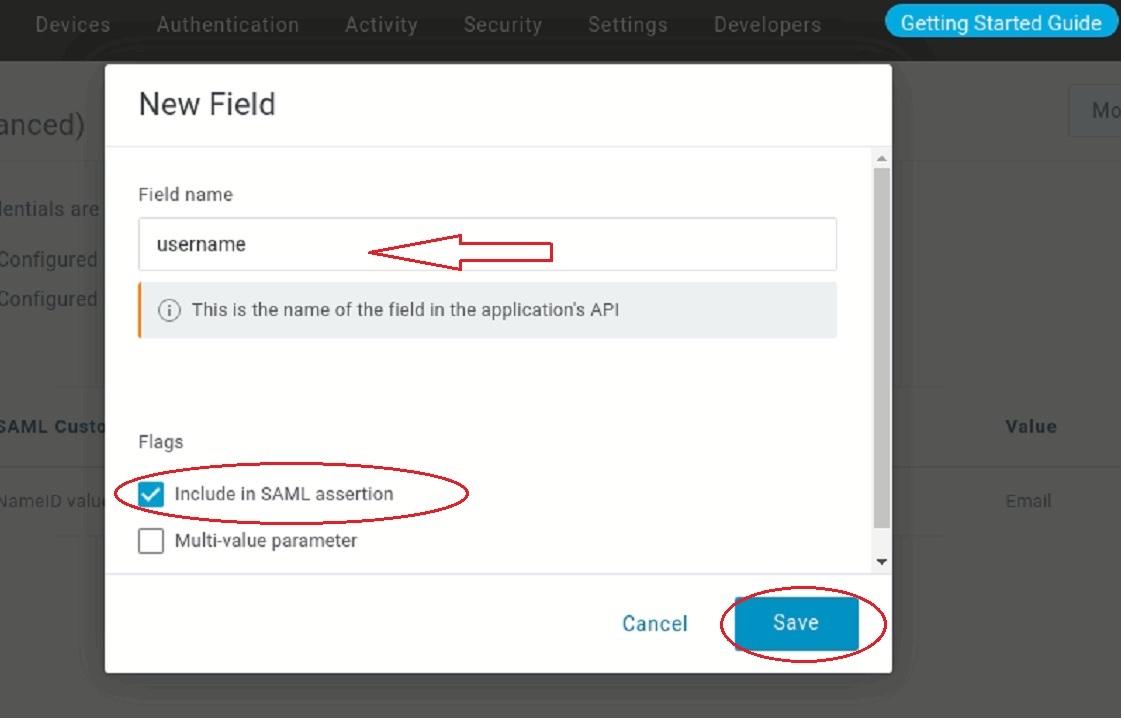
- Click Save.
- Choose the Username from the dropdown as the Value.
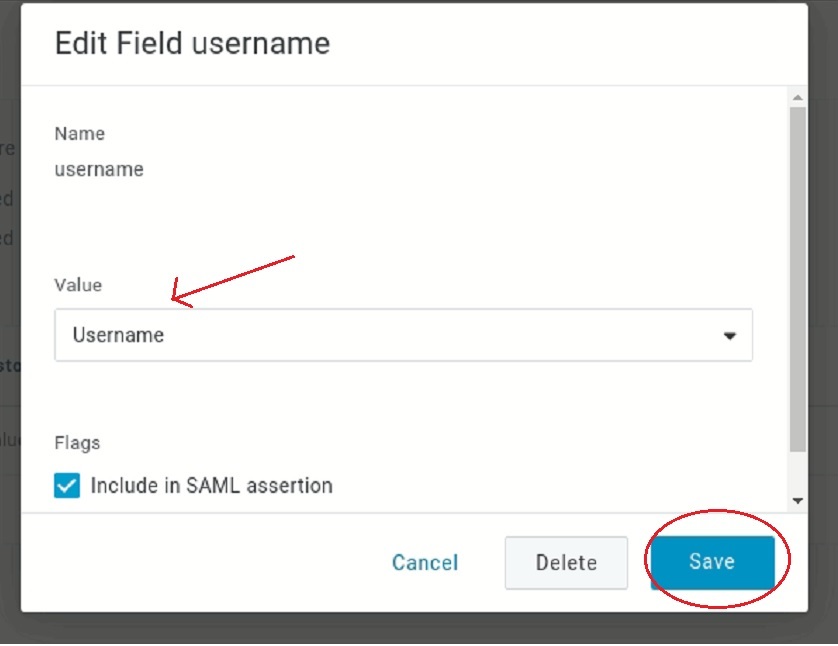
- Click Save.
- Type
-
In the SSO tab:
- Copy the Issuer URL. You will enter this in the Metadata auto conf url field in Device42.
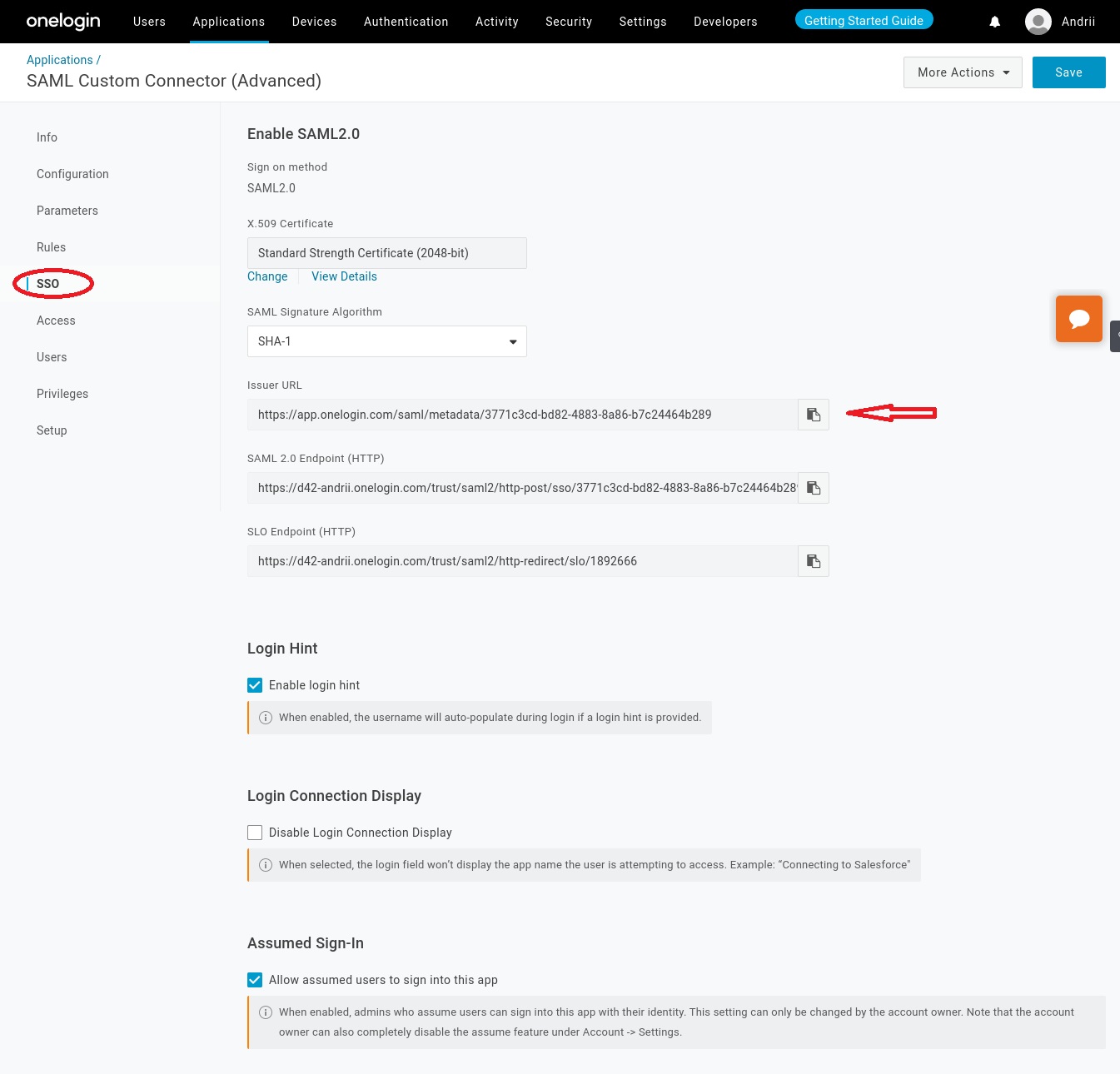
After this, the SAML2 app is created and ready to be integrated with Device42.
Configuring the Device42 Appliance Manager
-
Log in to the Device42 Appliance Manager,
https://yourdevice42address:4343, go to SAML/SSO settings on the left, and set the Metadata auto conf url you obtained above.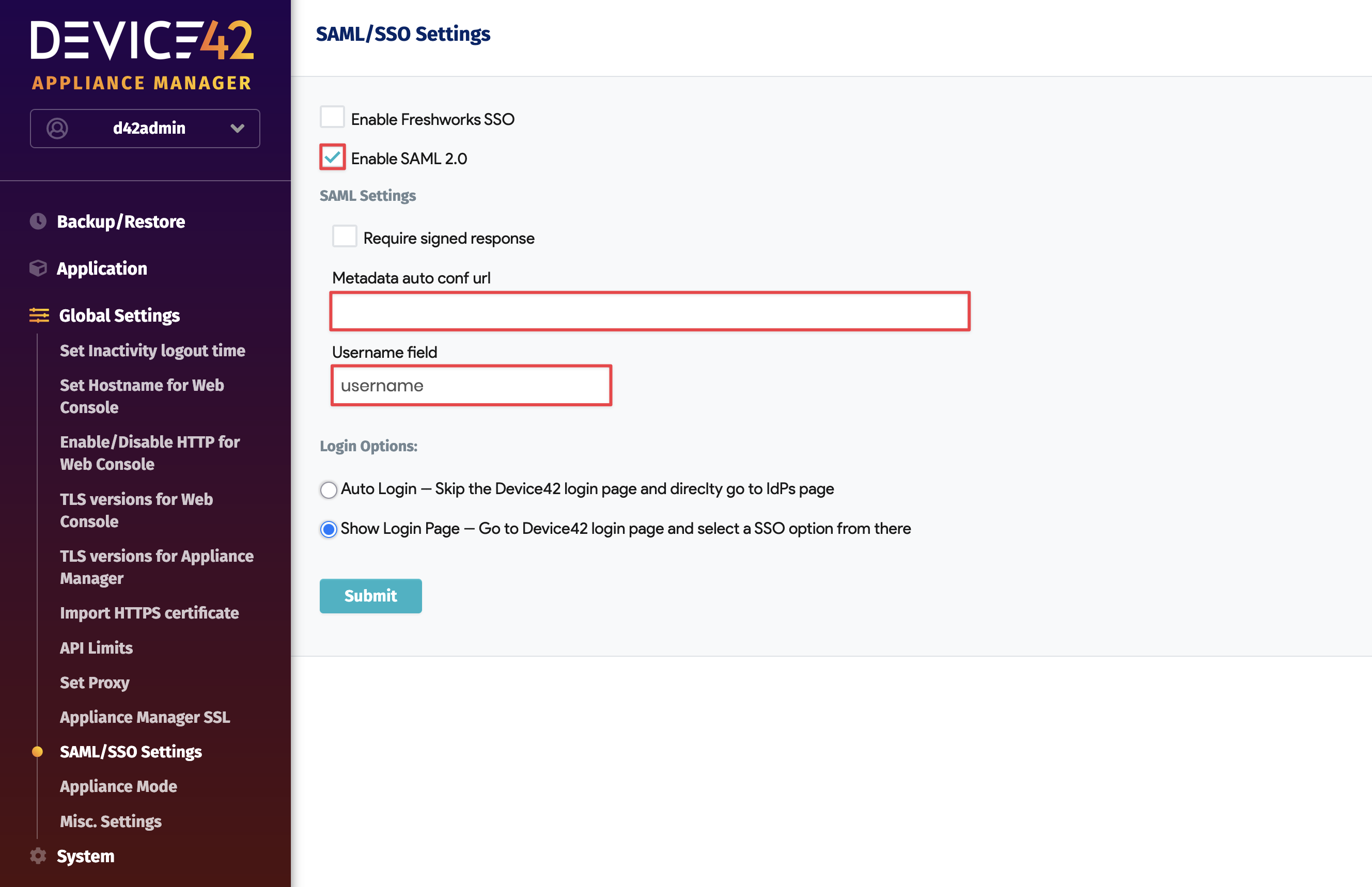
After this has been saved, the SAML integration should be complete. You now need to add users to the SAML Connector App so they can log in to Device42 via their OneLogin accounts.
Creating a User in OneLogin
-
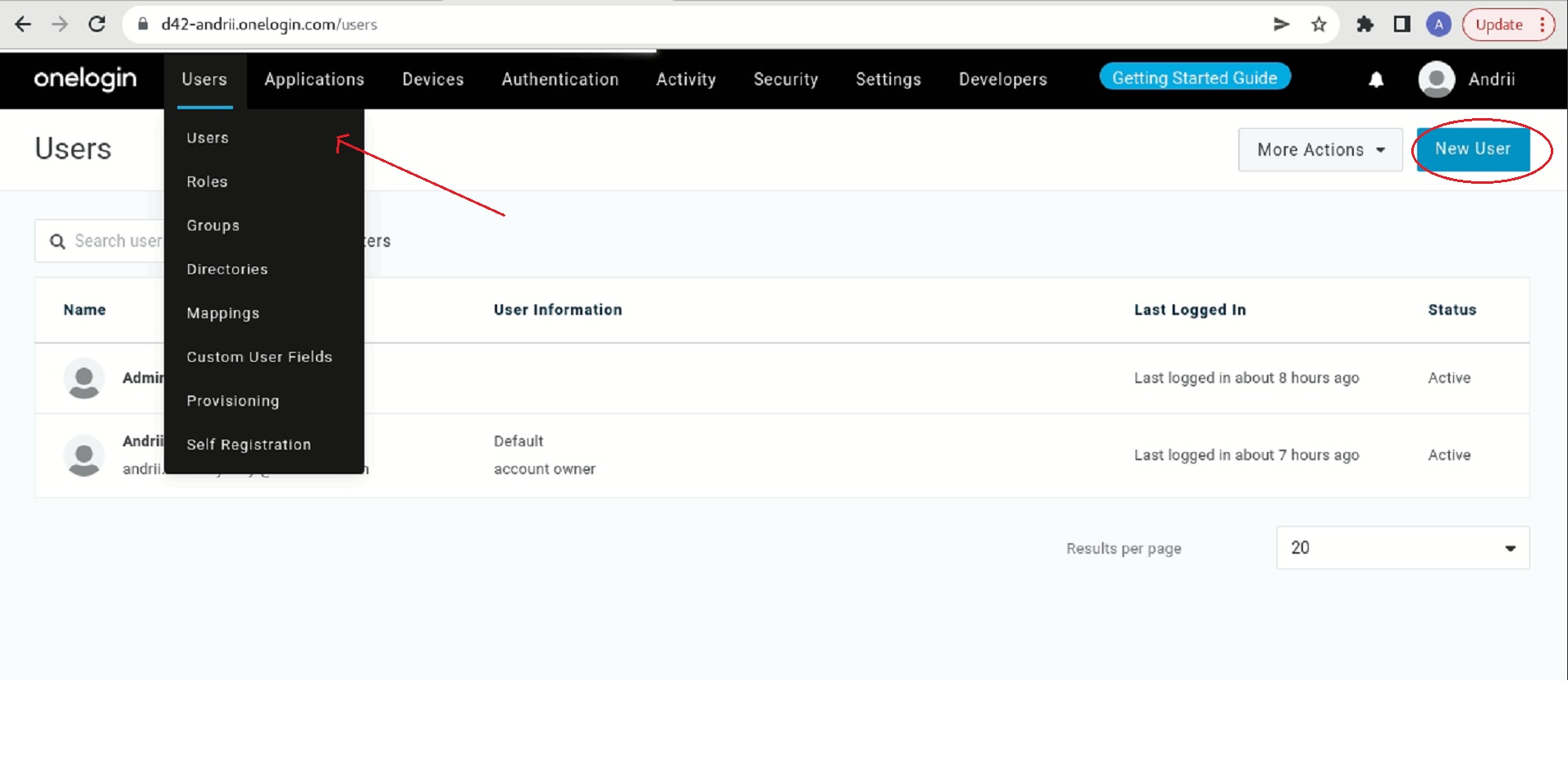
Go to Users > Users.
-
Click New User.
-
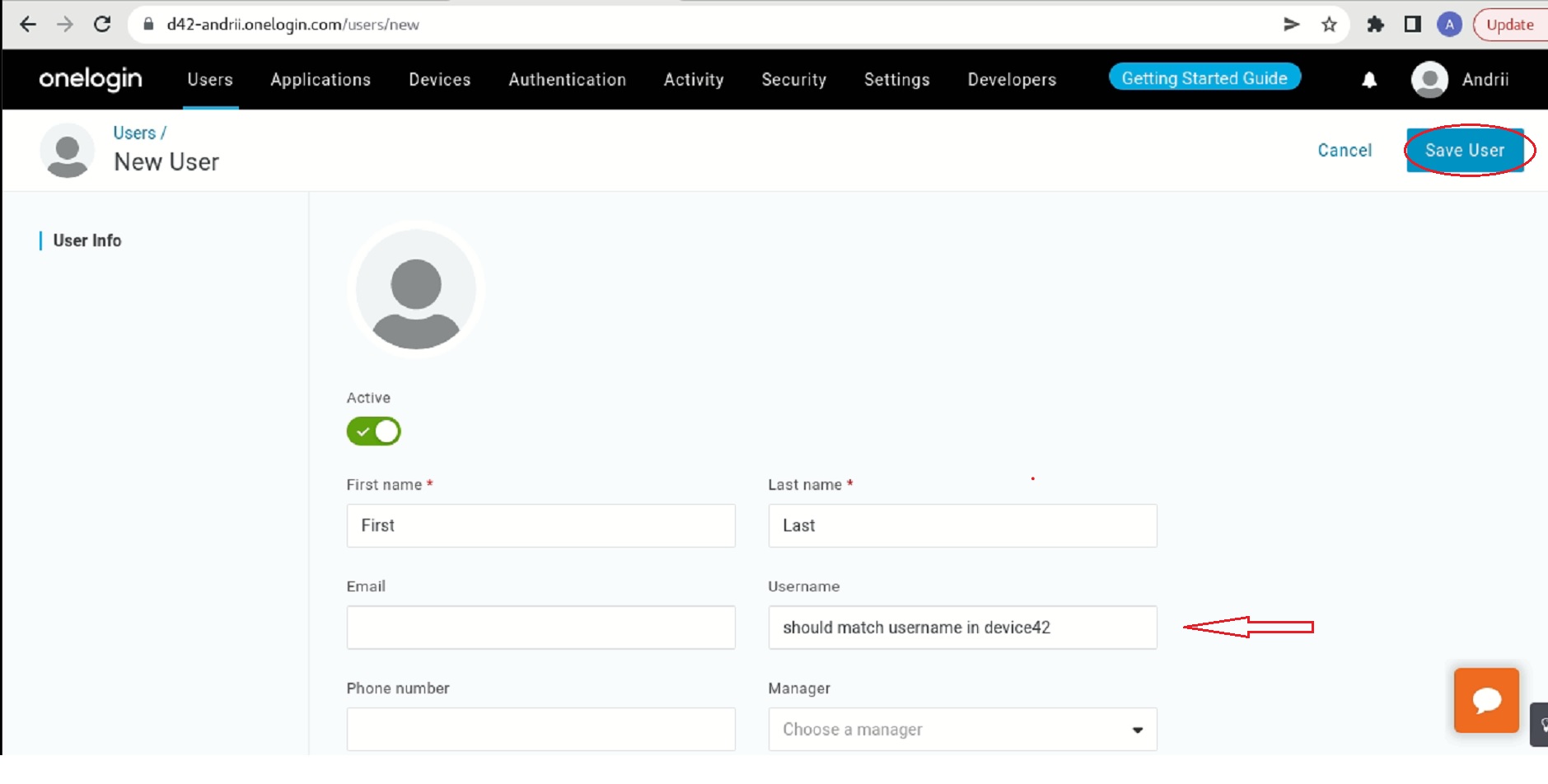
Fill in the form. The username should match the username in the Device42 app.
-
Click Save.
Adding a User to the Application
-
Click on the username.
-
Go to the Applications tab and add an Application by clicking on the plus icon.
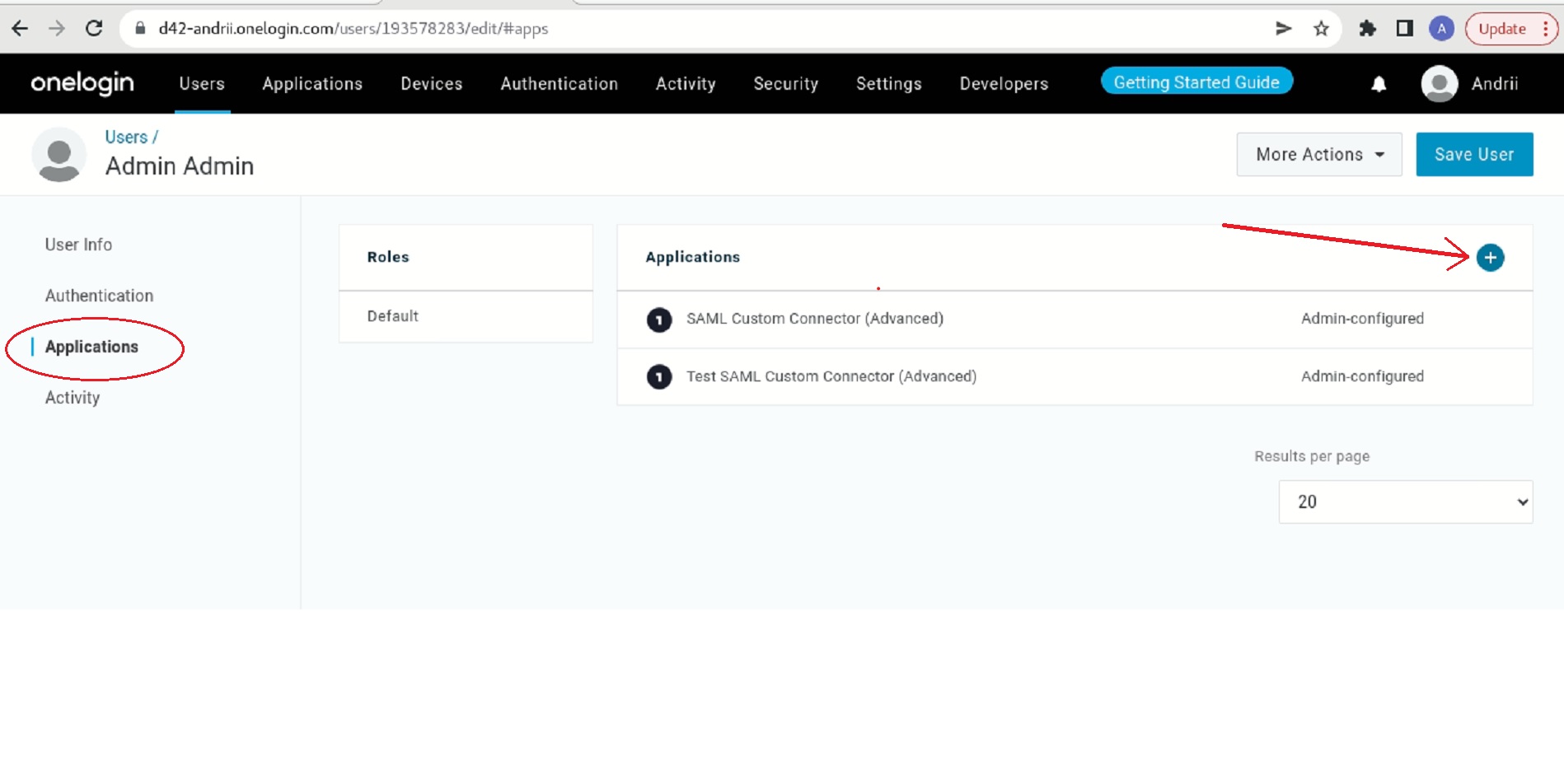
- Select the SAML Custom Application created above.
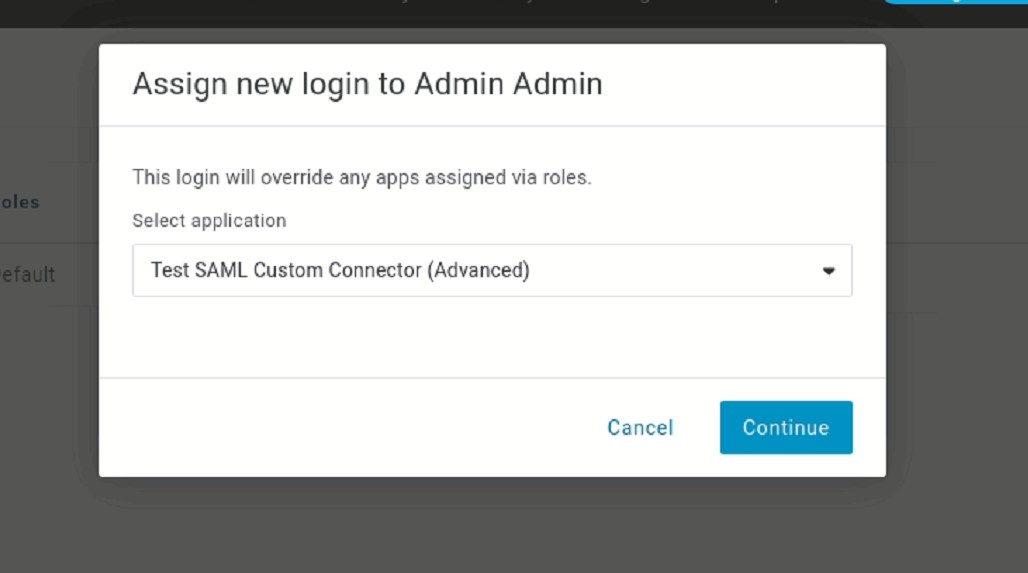
- Click Continue.
- Make sure the Allow the user to sign in checkbox is selected.
- Click Save.
Now you can log in to Device42 using the OneLogin account.
Device42 Appliance Manager Configuration
Log in to Device42 Appliance Manager, https://yourdevice42address:4343, go to the SAML 2.0 Settings on the left, and set the Metadata auto conf url you obtained above. Set the Username field to match the value you saved in the SAML configuration.

After this has been saved, SAML integration should be complete!